Difference between revisions of "Build Backend Pool"
m (Unprotected "HOWTO:Build Backend Pool") |
|
(No difference)
| |
Revision as of 17:50, 1 July 2008
Contents
Summary
This page details how to scale your laboratory environment up to a pool of backend target machines available for remote access.
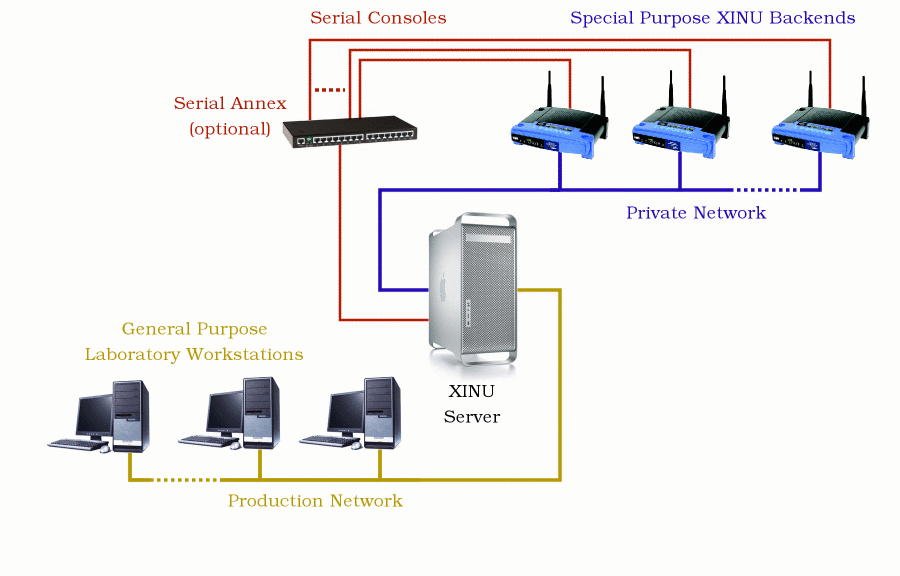
The Big Picture
XINU Backends
Backend targets upload a student's kernel over a private network on boot, and run the O/S directly. No simulations or emulation are involved; this is real hardware.
MIPS targets: We use Linksys WRT54GL wireless routers (~$60) with serial port modifications (~$10) running an embedded MIPS32 200MHz processor, 4 MB flash, 16 MB RAM, two UARTs, wired and wireless network interfaces.
PowerPC targets: We use Apple G3 desktops (recycled) with 512 MB RAM, linear framebuffer, PCI bus, NIC, HD. Apple G4 MiniMac also supported.
CISC targets: Classic XINU runs on Intel x86, Sun 3/Motorola 68K, Sparc, and VAX, among others.
XINU Server
A general purpose server with multiple network interfaces manages a private network for the XINU backends, using standard network protocols like DHCP and TFTP.
Backend serial consoles can connect directly to server's serial ports, or, in larger installations, to a serial annex or concentrator that allows many more serial ports.
A daemon running on the server allows users on frontend workstations to remotely access backend serial consoles, or upload fresh kernels. Optional rebooting hardware allows clients to remotely reset crashed backends.
Our Console Tools are freely available for modern UNIX platforms, including Fedora Linux and Solaris.
XINU Frontends
General purpose computer laboratory workstations can compile the XINU kernel, using a standard GNU C compiler and UNIX toolchain. GCC cross-compilers are readily available when the frontend architecture does not match the backend architecture.
Backend consoles can be connected directly to frontend serial ports, or frontends can communicate with the server daemon that manages collections of backend serial consoles.
With fully remote console access, kernel upload and powercycling, any machine on the network is a potential frontend, and need not be physically near the XINU server and laboratory hardware. Students can work on their operating system projects from their dorm room computers.
Additional (Optional) hardware
- Terminal Annex (EtherLite 32)
- Serial-Controlled Power Strip (BayTech)
- Serial adapter diagrams
The Server
Our XINU Server is a PowerPC G5 XServe running Fedora Core Linux. We use this configuration as a model for the information below, but other architecture / O/S combinations are known to work, and there's no reason this shouldn't work for virtually any machine with two network interfaces running a modern UNIX O/S.
DHCP Daemon
Many modern firmware implementations will allow a device to automatically acquire an IP address using the DHCP protocol even before the O/S kernel begins to boot. The CFE on our Linksys backends will attempt to configure its primary ethernet interface when issued the command,
ifconfig -auto eth0
over the serial console. See HOWTO:Build and Deploy XINU for more details.
In our configuration, the XINU Server runs a DHCP daemon that is configured to supply addresses to backends on the private network. We use the standard dhcp server package that comes stock with our Linux distribution (dhcp-3.0.5-3.fc6, as of this writing). Here is a sample configuration file, dhcpd.conf. Our configuration supplies a fixed IP address for each backend, based upon MAC address. It is important to note that the "filename" field designates a unique boot image for each backend; this allows each backend to boot a distinct image, customized by the student currently connected to that backend's serial console.
TFTP Daemon
Many modern firmware implementations will allow a device to upload a boot image over a network device using the Trivial File Transfer Protocol (TFTP). We use the stock TFTP server available with our Linux distribution (tftp-server-0.42-3.1, at this writing,) configured to answer requests on the private network, and with the /tftpboot directory writable by the xinu-console daemon user ID. Most TFTP daemons use TCP wrapper to regulate access; see the notes on security below.
Xinu Console Daemon
The Xinu Console Daemon and various associated utilities provide network clients with connectivity to backend consoles that are really only connected directly to the console host. It is freely available from the downloads page.
The Xinu Console Daemon uses TCP wrappers to prevent unauthorized access; see the notes on security below.
The Client
Console Access
Source for xinu-console included in Console Tools tarball. Explain environment variables. Ssh tunneling? Mips-console wrapper script.
Security
A word on security. Isolated private network. TCP Wrappers. Iptables packet filtering.